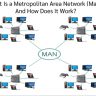
Know More About the Metro Ethernet
The Metro Ethernet is a kind of computer network system which aims to connect various subscribers as well as various business people together on the internet network. Moreover, with this system, you can also get a chance to connect with the service network. Through this system, many people can get connected together with one service network.
In the metropolitan cities, nowadays, you will see these kinds of network systems in places like big offices or schools. There are plenty of reasons for the popularity of this network. Here we will discuss some of these factors.
The first and the foremost reason is its low cost. Generally, compared to other networks it is quite economical. The reason behind this is its simple design, the system uses a kind of technology called the layer 2 switches and this makes this it very effective yet affordable.
Some of the basic advantages …