computer network tutorial pdfA personal computer network is the practice of linking two or far more computing devices together for the objective of sharing data. Today’s networks generally employ UTP (unshielded twisted pair) cable. It resembles, but ought to in no way be confused with, phone cable. The tight twist of each pair is tightly spec’d and is what offers it noise immunity. For most data networks, Category 5e or 6 rated UTP cable is used. My recommendation is that in new construction, all communication cable, whether or not intended for information or voice, should be at least Category 5e UTP. The cable that’s permanently installed in walls, ceilings, and floors should be solid (not stranded) conductor.
The principal benefit of a peer-to-peer network is the decrease setup expense. There is no require for investing in a pc which will act as a server. If the computers in your office currently have an operating method like Windows, Mac OSX or Linux, it will most possibly demand reconfiguration to be used as a network program. This will also assist to bring expenses down. Apart from, it will make the setup a lot faster and less complicated. Another benefit is that each and every user will have greater handle more than the program.
Some firms use a local location network in such a way they are very dependent on it usually working. If the company’s network fails, then you may possibly see all the personnel chatting away in the corridors simply because they can not do their perform. This indicates massive losses for the business and causes stresses on the employees. All firms must contemplate their regional region networks a essential asset and downtime must be avoided. This imposes enormous demands on the network employees to maintain such networks operating almost one hundred% of the time.
The Role Of Input Devices In Pc introduction to computer network powerpoint
introduction to computer networks and cybersecurity pdf free downloadIn a nutshell, laptop networking is fundamentally a cluster of computers linked collectively in a way that it can transmit information and share sources. Personal computer Networking is the art of connecting two or much more computer systems in order to share peripherals (resources) for instance printers, faxes, photocopiers, CD ROM, and information among other folks. Therefore a personal computer network will be the interconnection of two or much more computer systems. A personal computer network can also be defined as any collection of independent computer systems that exchange details with each other over a shared communication medium. This Introduction to Pc Networking guide will support you get the information you are looking for.
Step three: Adjust your SSID. Your SSID is the name that you see for your wireless network when you search for open networks making use of a Wi-Fi enabled device. If the SSID is set to the manufacturer’s default, any person looking for an open network nearby can see yours, and with a tiny searching on the world wide web they can figure out the model number of your router which will help them acquire access to your router’s settings.
Peer-two-Peer networks let each and every personal computer to select what details will be shared. There is no main server where it is all stored, every tough drive is open to the network and each and every pc on the network will be given the proper access to the difficult drives on every single technique. Most property users have the peer-2-peer network setup where they can choose and choose what details is needed or wanted from each and every method in the property on the network. Most businesses use the client-server network with distinct topologies or structures or designs within their layouts.
The problem with Microsoft was that it was unable to adapt beyond the original concept of a laptop. Instead of changing its emphasis towards new technologies such as internet based applications and diversified devices, it attempted to enforce its trademark against the competing forces by leveraging the power of its marketplace penetration, a strategy which has served well over the preceding years. But you cant resist the forces of evolution, ask the dinosaurs, for that reason alternatively of spearheading the technological revolution, and molding its industrial shape for the future (considerably like it had at the onset of the individual personal computer), Microsoft was condemned to backtrack against its original method and model the technology of competitors when inferior, such as the graphical design of OS X for Windows Vista. Moreover the organization jumped on the net wagon also late, was unable to neutralize Google and is now stuck with Yahoo.
There are two principal categories that define the make up of cyber-crimes. Firstly these that target laptop networks or devices such as viruses, malware, or denial of service attacks. The second category relate to crimes that are facilitated by pc networks or devices like cyber-stalking, fraud, identity-theft, extortion, phishing (spam) and theft of classified data.
The globe of computers is made up of computers and other networking devices interconnected together with wires while other folks are interconnected wirelessly to type what we call a network. A pc network is an interconnection of two or much more computers in order for the user to share information and peripherals. There are so a lot of diverse types of pc networks in existence.
On the matter of fact that personal computer network has created the lifestyle of many very smooth and simpler, there are certain downfalls of networking. A variety of hackers may try to hack the important files and data from laptop networks. Additionally, the networks can have technical concerns that can create significant troubles. In order to protect the information related to an individual, organization or government physique, networking specialist are broadly in demand.
World wide web: It is a network of computers in the planet. You can browse by means of much much more info than you could do in a library. Via E-Mail you can communicate with a person sitting thousands of miles away in seconds. There is chat computer software that enables a single to chat with yet another person on a actual time basis. Video conferencing tools are becoming readily obtainable to the widespread man.
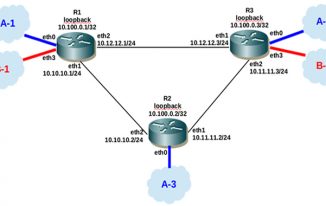
Pc Network Topology computer networks basics tutorials point
computer networks a systems approach pdf downloadComputer network installation has become an crucial prerequisite for any effective modern-day business as it allows staff to genuinely operate as a group by sharing data, accessing the very same database and staying in touch consistently. In its simplest type, a NAS unit can be any unit attached to a network for storage purposes. When upon a time, this was a server – a computer especially setup to serve data. Nevertheless, servers had been really costly. Most property owners could not justify the fees of these devices, limiting their effectiveness to company applications in most situations.
2.Security Policy. Technology is but a tool in the enforcement of specific rules that are meant to preserve your information secure and your organization running smoothly. A security policy must consist of various guidelines and behaviors, such as a password policy requiring users to have passwords that can not be very easily guessed or broken and firewall rules permitting distinct targeted traffic in and out of the network. It is extremely advised to seek advice from with a network safety specialist when compiling a security policy for an workplace with a lot more than ten users. It is needed to enforce the policy once it has been created, to ensure its effectiveness. The Fundamentals The following three resources are a should for any single computer or network connected to the Internet.
With the most recent developments of technologies, it is practically impossible to maintain the pace with this technological development, specially with laptop technologies. New personal computer software program are introduced each and every day and several old computer software are updated into new versions due to which it is often turn out to be a challenging job to operate a file or program with old versions. Here are handful of methods provided to preserve you up to date with most recent version of software.
Just as the net has empowered activists and revolutionaries to rise up against oppressive regimes, it has also empowered terrorist networks such as Al Qaeda to spread their propaganda and radicalise Muslim youth across the planet. It enables anybody with a personal computer to learn how to make a bomb, speak to like-minded groups and organize themselves against the state and society. Already the main enemies of the western world appear to be loose-knit groups of men and women who have turn out to be empowered by technology to take on the most effective nations in the planet – rather than other nation states. In the future this trend could continue, with the 3D printing of weaponry threatening to make arms manage impossible, and DIY ‘open source’ biotechnology raising the possibility of house-created and novel biological weapons.
The history of the personal computer is 1 of visionary entrepreneurs who had been in a position to make offered to the public an evasive technologies. The quite 1st computer systems were not at all user friendly, in fact their use was restricted to the commercial sphere. It was not until Bill Gates invented a graphical interface with Windows that computer systems took the type below which we now use them.
Of the 53,000 viruses that have been identified and classed, a lot more than 80 percent of them have been classed as malicious and capable of harming your personal computer method or information files. These pc viruses behave in much the very same way as biological viruses by contaminating any computer systems they come in make contact with with. These self-executing applications are usually quite modest and function at damaging the way your pc functions or by damaging or entirely removing key program files.
Network refers to your computer’s network interface. If you are wired into your home’s network, it would be referred to as the Ethernet adapter. Nonetheless, if you are making use of a wireless access point, then you are making use of a wireless network Interface. Most individuals just contact this WiFi interface. The speed of the network is measured in Mbps (or mega bits per second). Most Ethernet adapters run at one hundred Mbps, and even 1000 Mbps. Wireless speeds vary. It can be anywhere up to 300Mbps. If your wireless signal is poor, it can do down as low as 1Mbps.
The data packs are also employed in personal computer that is when we connected with web this data pack helps to download the web pages that is becoming displayed in the monitor. For a Data Pack it does not need any separate path for downloading or displaying any objects in the computer or any other equipment. This is due to the cause that by networking, separate paths are becoming designed and soon after analyzing every single, the information are being transferred to the appropriate access point.
Beginner’s Guide To Computer Forensics computer networks tutorial for beginners
computer network models tutorialspointComputer networking is a procedure of sharing information and shared sources between two or much more connected computer systems. There are also a couple of security limitations which hackers can exploit to lead to harm in a wireless network. But Wireless technologies with greater safety features have started to come out. So this is not going to be a issue for extended. Speaking of progress, Wireless technologies is not limited to strong computers and mobile handsets. The technologies has progressed sufficient that Wi-Fi enabled TVs and microwaves have started appearing in the markets. The latest and the most talked-about wireless technologies is the NFC or Near Field Communication, which lets customers exchange information by tapping their devices together. Using wireless technologies are not as high-priced as it used to be in the last decade. With each and every passing year, newer and much better wireless technologies arrive with higher advantages.
Think about the portion of the address that contains the string of 1’s as the masked portion. Think about the portion of the address that includes the string of 0’s as the unmasked portion. Recognize that with class C addresses, the only octet we’re interested in, in terms of producing subnetworks, is the final one for the address, we are interested in the masking and not masking of the 11000000 octet. Right here we can see that two bits have been masked to develop subnetworks and the remaining 6 bits are unmasked and consequently used for host addresses on the aforementioned subnetworks. I will show you how to perform out how numerous subnetworks and hosts per subnetworks this creates, but first I will give you a lot more of an insight into converting dotted decimal addresses (255.255.255.192) into binary notation.
The breakthrough in technology specifically in the 21ist century is more evident in the emergence of different varieties of personal computer systems. Every sort of personal computer is met to serve a purpose. There is the general believe that all computer systems are the exact same. You will learn a clear distinction at the finish of this discourse.
Tiny to medium size enterprises are also in want of this service, but oftentimes a permanent, in-home arrangement is not economical. For this purpose, network assistance,computer tech support & safety firms exist. They offer you a much more cost successful strategy to computer safety. Rather than keeping a permanent organization to address the problem, these groups can set up the necessary security protocol and do safety check and upgrades on a periodic basis.
Although the mechanisms for attack may possibly differ according to the kind of worm, every of the worm kinds nevertheless exhibit characteristic worm behavior, chief of which is self-propagation. Worms spread amongst hosts and networks employing the resources of the infected host and do not demand the aid of a file to infect for transport as is the case for standard viruses. Some worms exhibit stealth technology creating these worms tough to detect and clean from infected systems.
I got sophos for my mac beascue I never want to be spreading about Pc viruses by accident. I have discovered a couple of times that an Email I have gotten has had a virus in it and I would not have recognized about it. I guess you can say that I stopped my friend’s computer systems from obtaining the virus. I also think it is a great concept to have the computer software there just in case. I’d rather put a lock on my door and place a very good security technique in location so that the negative guys will not get in once they commence attempting to do so.
Due to the fact these viruses copy themselves to any computer program they come in make contact with with, the spread of viruses throughout a personal computer network or the Internet is a really quick and deadly thing to take place to your laptop. Since personal computer viruses are a hot topic, they routinely are the subject of magazine articles and forum subjects on the web. Whilst some viruses do practically nothing more than frustrate you with pop-up ads or other messages, others are entirely malicious and set out from the start off to destroy the files and operating systems of your computer.
Lately nonetheless, there has been a dramatic shift in the nature of the goods accessible on the industry. The private computer no longer is a common of reference, instead there are a number of applications of the technologies. From smartphones, to tablets, to image frames, to intelligent TVs and alarm clocks, to all sorts of interactive surfaces such as digital whiteboards. In addition the market place for computer software is also experiencing a revolution, the box based title is becoming much less and less popular to the profit of internet primarily based platforms such as social networking internet sites, remote desktops and cloud computing.